The rise of mobile banking has provided a myriad of benefits for customers, offering convenience, speed, and flexibility. However, this evolution has opened the door for malicious actors to exploit these systems for fraudulent activities.
Drop Accounts – Building Credit for Synthetic Identities
A form of this exploitation involves the use of mobile devices to create ‘drop’ bank accounts for synthetic identities. Fraudsters, often leveraging stolen or fabricated personal information, utilize these accounts to establish a credible financial history for these non-existent entities. Over time, they build up credit for these synthetic identities, frequently going unnoticed due to the seemingly legitimate activity.

The ultimate goal is to leverage this falsely established creditworthiness to secure substantial loans or credit lines, only to default on them later, leaving banks and their customers to bear the brunt of the substantial losses. This complex and sophisticated fraud scheme exposes a significant vulnerability within the banking sector, posing substantial risks to financial institutions and their customers alike.
How Does Phone-Based Identity Verification Enable Drop Bank Accounts?
Continuing from the problem, an additional layer of complexity emerges when considering how fraudsters acquire multiple mobile devices to further enable their deceptive practices. In today’s market, prepaid or ‘burner’ phones can be purchased easily and anonymously, providing fraudsters with the tools they need to validate and authenticate synthetic identities.
The possession of a unique phone number can serve as a robust verification method in many identity verification processes. By associating each synthetic identity with a unique phone number, fraudsters can bypass phone-based or possession-based identity verification checks implemented by banks and other financial institutions. This verification process often involves sending a one-time password or a verification link to the registered phone number, which the fraudster can easily access and validate, thereby ‘confirming’ the legitimacy of the synthetic identity.
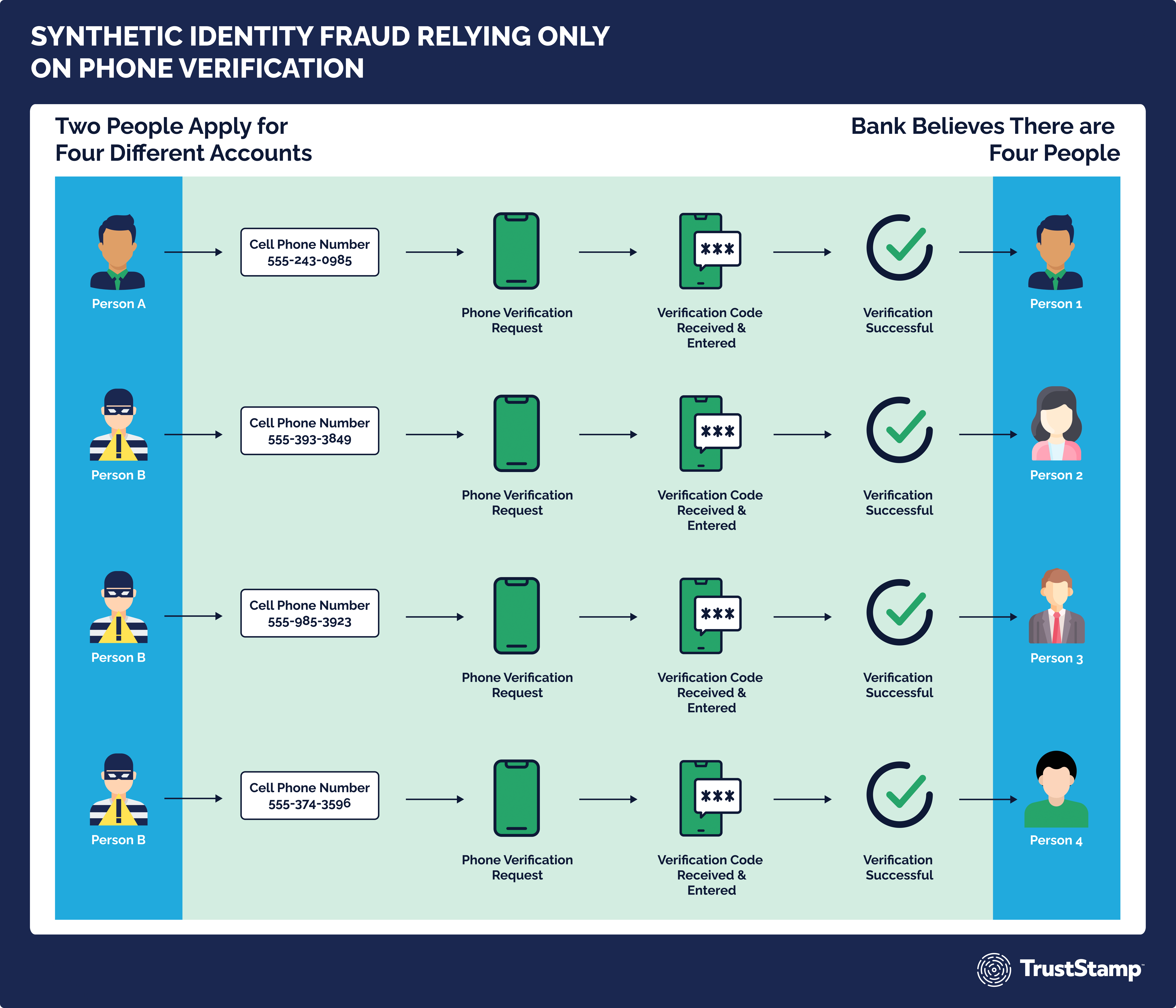
In this way, fraudsters exploit the very mechanisms designed to ensure security, using them instead as a means to legitimize their fraudulent activities, further escalating the risks and challenges faced by financial institutions in their ongoing battle against identity fraud.
Biometrics: A Powerful Countermeasure Against Synthetic Identity Fraud
In the face of these escalating challenges, the introduction of biometrics as an additional verification factor presents a promising solution. Biometric authentication utilizes unique physical attributes to confirm an individual’s identity. This form of authentication offers a significant advantage over possession-based methods, as biometric features are inherently tied to the individual and cannot be easily replicated or stolen. Especially when robust replay attack detection/liveness detection features are implemented.
By adding a biometric layer to the authentication process, financial institutions can significantly reduce the risk of synthetic identity fraud. When a new account is created, the individual’s biometric data is captured and linked to their identity. Any subsequent transactions or interactions would require biometric verification, ensuring that the person accessing the account is indeed the registered individual. This can be added to existing possession or phone-based identity verification.
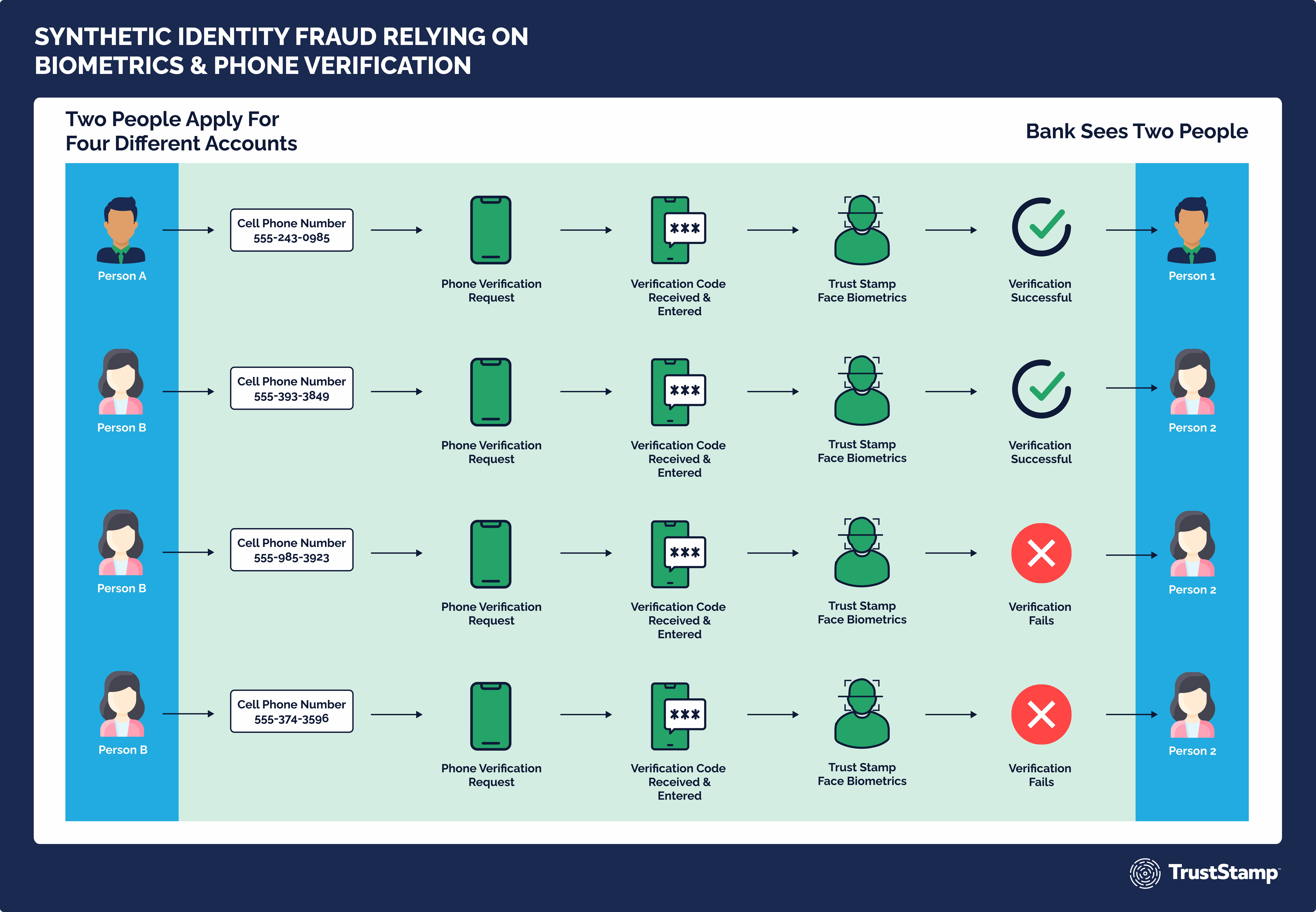
In the case of synthetic identity fraud, where the fraudster is attempting to create a credible financial history for a non-existent entity, the addition of biometric data makes this far more difficult. Since each set of biometric data is unique to an individual, creating a synthetic identity that also possesses a believable set of biometric data becomes a near-insurmountable challenge for fraudsters.
The key is to increase authentication factors by adding a third factor that is independent of the device itself.
Trust Stamp’s Identity Verification and Biometric MFA add a low-friction and third authentication factor of a facial biometric. New bank customers can walk through a digital and remote KYC process where their identity is verified through a selfie and a picture of their driver’s license. After this, a user’s biometric is established, and duplicate identities can be detected.
This prevents the type of synthetic identity fraud perpetrated through drop accounts and burner phones.

