Account takeover (ATO) is a growing threat, with attackers exploiting weak recovery processes to bypass strong authentication methods. ATO incidents surged in recent years, causing significant financial losses and data breaches. No matter how strong the authentication may be, a weak account recovery process when someone forgets their username or password or gets a new device can undermine the entire system. Companies face a significant challenge—implementing account recovery processes that prevent fraud without creating customer friction. Trust Stamp’s Stable IT2 addresses this by securing both authentication and recovery, eliminating the weak links that lead to account takeovers.
Complicating this, the average internet user is locked out of 10 accounts per month, often struggling to recover them via methods that are tedious and open to exploitation, struggling with traditional recovery methods that can take valuable time and leave accounts vulnerable. Without strong protections in place, attackers exploit these vulnerabilities for account takeovers, making recovery a critical weak point in overall security.
Account Recovery Vulnerabilities
Account recovery is typically initiated when a user loses access to their credentials—whether it’s a forgotten password or lost access to their device. Unfortunately, these recovery methods are often weak links in an otherwise secure system. Traditional identity verification methods used during account recovery can easily be exploited by attackers, leaving sensitive accounts vulnerable to fraud and breaches. For example:
- KBA security questions: Personal answers, like a mother’s maiden name, are easily phished or found online via data breaches.
- Email reset link risks: If a fraudster controls the email account, reset links become a single point of failure.
- OTP capture: Trojans, SIM swaps and bots intercept OTPs, exploiting application weaknesses.
- Phishing for credentials: Generative AI has enhanced phishing attacks used for socially engineering credential theft, making these attacks more sophisticated and harder to detect.
- Voice deepfakes: Fraudsters use AI to clone voices, bypassing voice authentication systems.
- Fake IDs: High-quality forgeries can pass ID document checks, leading to fraudulent account recoveries.
Multi-Factor Recovery with A Biometrically Bound Passkey through Trust Stamp’s Stable IT2
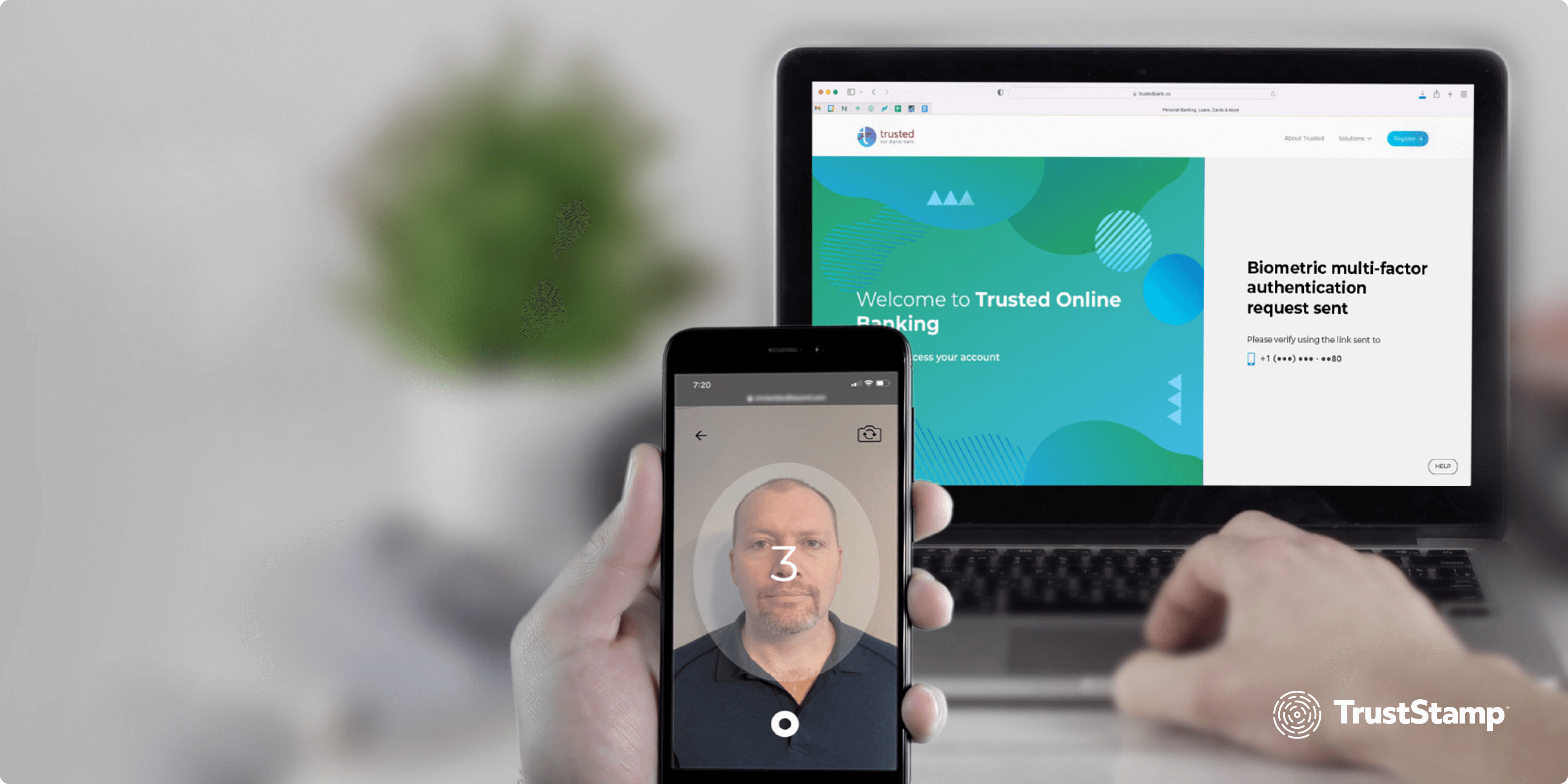
Given these vulnerabilities, traditional account recovery methods expose users and organizations to significant risks. To prevent account takeovers and secure recovery, a more resilient process is required—one that addresses the weaknesses of outdated methods. Trust Stamp’s Stable IT2 offers a robust multi-factor recovery solution that retains the existing knowledge factor (e.g., passwords), while adding both a biometrically bound passkey and a biometric factor, making traditional authentication a minimum of three factors and account recovery at least two factors.
Trust Stamp’s Stable IT2 facilitates a transformative approach to account recovery by requiring not one, but multiple factors for both authentication and account recovery. By binding both biometrics and a passkey to the user’s identity, Stable IT2 ensures that only the rightful account owner can regain access—even in the event of a lost password or compromised account.
This multi-factor approach introduces a higher level of security for recovery:
- Biometric Authentication: The user’s unique biometric data (such as a palmprint or facial scan) is bound to their identity, ensuring that recovery cannot be initiated without their physical presence.
- Passkey: Trust Stamp’s technology provisions trusted devices with a secure passkey. An identity is authenticated only when the user provides both the passkey stored on a provisioned device and a live matching biometric. This dual requirement ensures that even if one factor is compromised, the account remains protected, as access can only be granted through the combination of a trusted device and the user’s biometric data.
By combining multiple factors, Trust Stamp’s Stable IT2 eliminates the weaknesses associated with traditional account recovery, ensuring that a forgotten password or compromised email can no longer provide unauthorized access.
Why Biometric + Passkey Recovery is the Future
The combination of biometrics and passkey not only strengthens authentication but also brings an unparalleled level of protection to the account recovery process. Here’s why this approach is critical:
- No Single Point of Failure: Traditional account recovery methods often rely on a single factor, such as an email or phone number. If this single factor is compromised, the entire account is at risk. With Stable IT2’s two-factor recovery, both biometric data and the passkey must be verified, significantly reducing the chance of unauthorized access.
- User-Friendly Security: While two-factor authentication (2FA) can sometimes complicate the user experience, Stable IT2 integrates seamlessly with biometric systems to provide security without sacrificing convenience. Users can enjoy fast, secure access without needing to manage additional codes or devices.
- Privacy-Preserving: With Stable IT2, biometric data never leaves the user’s device. This ensures that their sensitive information remains private and secure, aligning with the growing demand for privacy-preserving technologies in today’s decentralized identity landscape.
Adding Biometric Binding Without Compromising Privacy: Stable IT2’s Privacy-Preserving Solution
Trust Stamp’s Stable IT2 strengthens account recovery by incorporating biometrics without compromising user privacy. Unlike traditional systems that store sensitive data, Stable IT2 ensures that biometric information never leaves the user’s device. It transforms biometric data into secure, non-reversible tokens that cannot be reconstructed or misused. This approach enhances security while protecting privacy, offering organizations a way to leverage biometric authentication without exposing users’ personal data to central servers or potential breaches.
Strengthening Account Recovery with Stable IT2: Enhanced Security, Streamlined User Experience
As organizations grapple with protecting client accounts from unauthorized access at both the authentication and recovery stages. Trust Stamp’s Stable IT2 enhances account recovery by using multiple factors without introducing more steps for the user.
To learn more about how Trust Stamp’s Stable IT2 can secure your accounts, contact sales@truststamp.net today!

