As the digital landscape evolves to blend physical and online transactions into a seamless experience, security threats such as impersonation attacks and account takeover (ATO) are on the rise.
The convergence of many domains, including banking, healthcare, education, travel, and entertainment, requires frequent verification of our digital identities across numerous vendors. Unfortunately, this situation provides hackers and cyber criminals with increasing opportunities to intercept and exploit our identities for their gain, disrupting our lives and creating losses across innocent parties. Consequently, securing our digital identities has become more crucial than ever.
To date, still many online accounts that contain our identity are secured using traditional single authentication methods, such as user name and password. Implementing multi-factor authentication (MFA) is an effective approach to secure our identities and protect against these cyber threats.
This article dives into the core principles of multi-factor authentication, examining its functionality and illustrating how it bolsters security for individuals and organizations alike.
What is Multi-Factor Authentication (MFA)?
Multi-factor authentication is a security protocol that requires users to provide two or more verification factors to gain access to a resource, such as an application or an online account. Multi-factor authentication is a core component of a strong Identity and Access Management (IAM) policy. Instead of just asking for a username and password, multi-factor authentication requires one or more additional identity verification factors, which decreases the likelihood of a successful cyber attack.
Why is MFA Essential for Businesses and Individuals Alike?
Amid the escalating prevalence of cybercrime, enterprises grapple with the potential consequences of data breaches, including reputational damage, operational disruption, and regulatory compliance violations. At the same time, individuals are increasingly wary of fraud, identity theft, and the erosion of personal privacy. Businesses that ignore these concerns can stand to lose business and customer goodwill. Implementing multi-factor authentication (MFA) is one of the most foundational methods to reduce the risk of these threats. Multi-factor authentication adds a required layer of protection, significantly enhancing security and reducing the risk of unauthorized access.
Traditional single-factor authentication using passwords is often the weakest link in security systems, susceptible to brute-force methods and theft by malicious actors. Furthermore, the widespread practice of using the same passwords across multiple accounts can lead to devastating breaches if a single account is compromised. This grants unauthorized access control leading to the exfiltration of private customer information, ransomware attacks, and account takeover.
Enforcing multi-factor authentication (MFA) with an authentication factor such as face biometrics or physical security keys can provide businesses with greater security and compliance. By employing a robust multi-factor authentication system, you can confidently safeguard your organization and your customers’ data from increasing cyber threats, enabling you to concentrate on core business functions with peace of mind.
How Does Multi-Factor Authentication Work?
Multi-factor authentication (MFA) works by requiring users to provide two or more independent verification factors to confirm their identity during the authentication process for improved security. For example, in addition to traditional usernames and passwords, some MFA systems generate a unique one-time passcode (OTP), a 4-8 digit code you receive via email, SMS, or an authenticator app for each login attempt.
Multi-factor authentication offers an additional security layer of defense, making it more difficult for unauthorized users to gain access to sensitive information or systems. These layers are also called authentication factors.
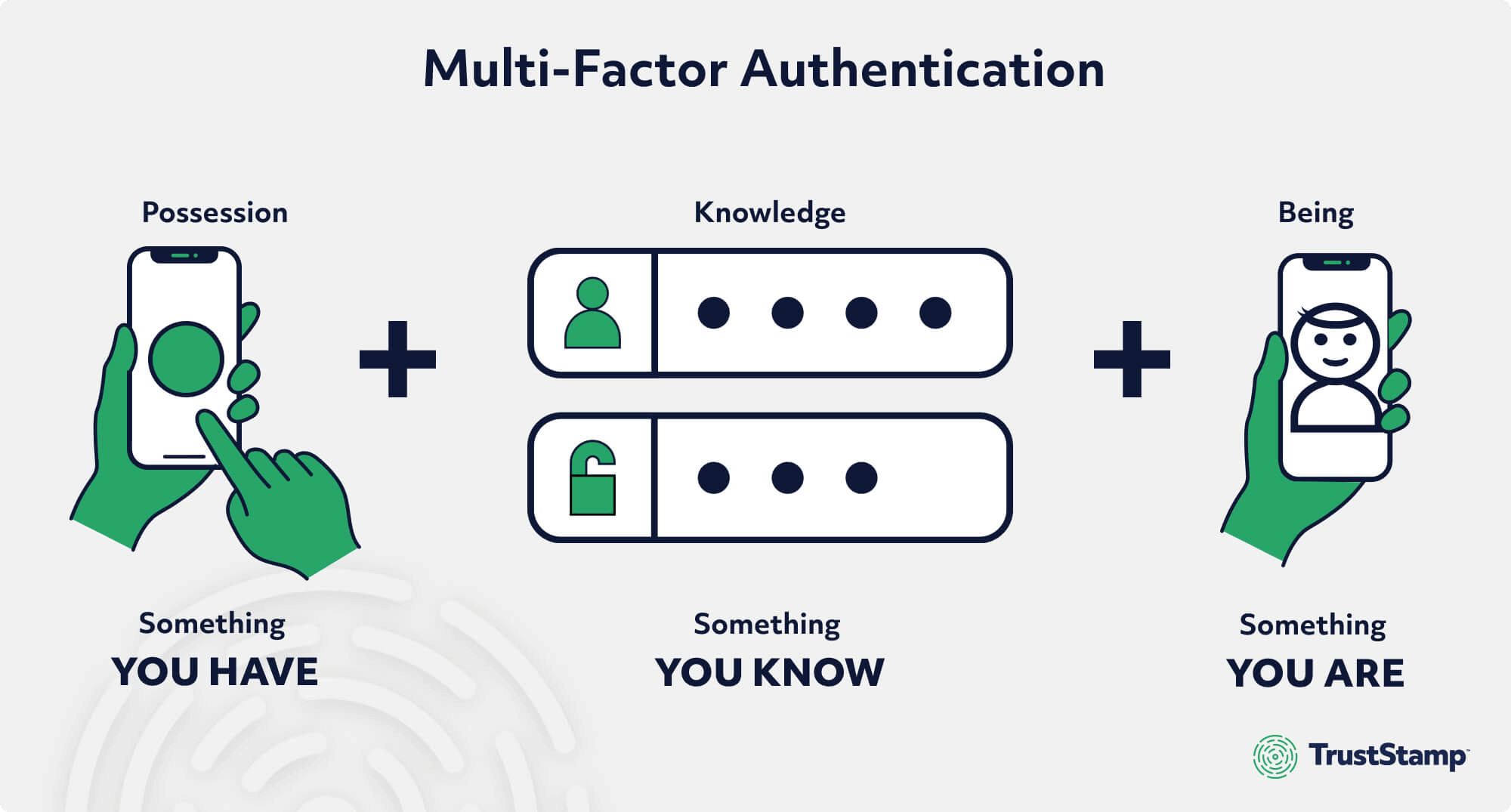
Types of MFA Authentication Factors
There are three main types of MFA authentication factors:
-
Something you know or Knowledge factors (e.g., password, PIN, or security question)
-
Something you Have or Possession factors (e.g., hardware token or mobile device)
- Something you are or Inherence factors (e.g., voice recognition, fingerprint scan, or face recognition)
Other Types of MFA Authentication Methods
With advancements in machine learning and artificial intelligence (AI), multi-factor authentication can also consider the following authentication methods:
-
Location-based authentication – A location-based authentication verifies the user’s identity by validating their geographic location, typically through IP address, GPS data, or nearby Wi-Fi networks. Systems can flag unusual or suspicious activities by comparing a user’s location with their previous login locations. For example, if a user logs in from two distant locations within a short time frame, it could indicate that their account has been compromised.
-
Time-based authentication – A time-based authentication factor is a security method that relies on time-limited credentials to verify a user’s identity. It is commonly used in systems where a link or a one-time passcode (OTP) is valid for a limited period of time, providing a additional security during the authentication process.
-
Adaptive MFA or Risk-based authentication – An adaptive authentication also referred to as risk-based authentication, analyzes the probability of account compromise with each login attempt. If the request seems unusual or suspect, the user is prompted to provide additional identity verification factors, such as biometrics, to gain system access.
Adaptive/risk-based authentication method confirms identity by looking at various information such as :
-
What is the user’s location when attempting to access information?
-
What type of device is being used? Has it been used previously?
-
Is the user attempting to access a system through a public or private network?
-
When is the user attempting to access company information? Is it during their regular working hours or outside of them?
-
By implementing a comprehensive MFA strategy, organizations can better protect their systems and data, protecting their organization and customers.
Protect Your Sensitive Data with Advanced MFA
Trust Stamp provides identity verification and biometric multifactor authentication methods. Trust Stamp’s privacy-first identity solutions provide biometric identity solutions without storing sensitive photos or biometric templates. Contact us today to secure your business and clients with advanced user authentication methods that can block hackers from accessing your sensitive data and your customers.

