As fraud threats continue their evolution, threats faced by call centers, particularly within the financial sector, are seeing a significant shift. A recent TransUnion report unveiled that 60% of financial industry respondents now identify call centers as the initial point for most account takeover incidents, a notable increase from 24% in 2021. In contrast, fraud attacks originating from web and mobile channels, which previously stood at 32% each in 2021, have decreased to 10% each in 2022. This transition underscores the need for advanced security measures to safeguard customer interactions and prevent unauthorized account access.
Call center fraud exploits vulnerabilities such as the limitations of knowledge-based authentication questions, the susceptibility of one-time passcodes (OTP) to interception, and the challenges faced by customer service representatives in identifying fraudulent actors, leading to significant security breaches.
Employing tactics such as spoofed phone numbers, social engineering, and exploiting personal information acquired through identity theft and data breaches to defeat KBAs, fraudsters have increasingly pinpointed call centers as a focal point for illicit access and account takeovers.
This blog post discusses what call center fraud is and the various ways fraud can be perpetrated in call centers. Furthermore, it elucidates why traditional knowledge-based authentication methods commonly used in call centers are no longer sufficient and how adding a biometric solution can transform how call centers verify customer identities.
What is Call Center Fraud?
Call center fraud is a scheme wherein bad actors assume false identities to deceive contact center agents into granting them access to sensitive data or account controls. These fraudulent actors often contact the call center armed with stolen or fabricated information, such as customer or employee details or credit card numbers. They aim to manipulate call center staff into providing access to genuine user accounts, controls, or information. Alternatively, they may attempt to impersonate the legitimate account owner and make fraudulent purchases and fund transfers.
Upon successfully impersonating legitimate customers, fraudsters’ objectives, though not exhaustive, typically encompass:
- Modifying account credentials to those within their control (such as phone numbers, mailing addresses, email addresses, etc.) effectively dispossessing the rightful owner from their account.
- Procuring personal data pertaining to users and customers, encompassing details of bank accounts, credit card information, and personally identifiable information
- Accessing and siphoning account balances.
- Eliminating fraud restrictions on the account to perpetrate a later fraud.
- Exfiltrating customer records, conversations, transcripts, and other sensitive data.
- Opening additional credit accounts by exploiting the information and access obtained by impersonating the legitimate owner.
Common Types of Call Center Fraud
Call center fraud encompasses a range of deceptive practices aimed at unauthorized access to customer accounts or sensitive information. Understanding these types is crucial for developing effective countermeasures. Below, we explore some prevalent forms of call center fraud, including Account Takeover, among others:
1. Account Takeover:
This form of fraud involves impersonators using stolen personal identifiable information (PII), such as social security numbers (SSN) and mother’s maiden names, to gain unauthorized access to users’ accounts. By masquerading as legitimate account holders, these fraudsters manage to lock out the actual users, altering login credentials or contact information to cement their control.
2. Card Not Present (CNP) Fraud:
Card Not Present (CNP) scams in call centers are perpetrated by fraudsters using stolen debit or credit card information to make unauthorized transactions over the phone, via Interactive Voice Response (IVR) systems, or online. Since the transaction occurs remotely, scammers do not need to present the card, bypassing the visual verification process physically. This type of fraud exploits the call center’s reliance on verbal or digital authentication, which does not include the physical inspection of the payment card.
CNP scam typically involves the fraudster contacting the call center, pretending to be the legitimate cardholder, and providing the stolen card details to make purchases or payments. The absence of physical card scrutiny allows these transactions to proceed undetected at the time. CNP fraud has become increasingly common with the rise in remote transactions, making it a significant concern for call centers and businesses relying on telephone and online sales channels.
3. IVR Fraud (IVR Mining):
Interactive Voice Response (IVR) Fraud, often termed IVR phishing or “vishing,” is a sophisticated scam targeting call centers’ IVR systems. This method involves fraudsters using pre-recorded messages or live calls to deceive individuals into handing over sensitive information under the guise of security verification or account updates. Unlike traditional phishing that relies on digital correspondence, IVR fraud leverages the more personal and persuasive nature of voice communication, making it particularly effective.
A typical IVR phishing scenario might commence with the fraudster pretending to be from a reputable organization, such as a bank, informing the victim of suspicious account activity. The victim is then prompted to verify their identity by providing sensitive details like card numbers or security codes. These details are harvested by the attacker, often under the pretense of protecting the victim’s finances.
The ‘Fake Bank Manager’ call is a common example of a vishing scam, where the fraudster, creating a sense of urgency about “suspicious activity” on the victim’s account, pushes for impulsive decisions. They aim to build trust and then request sensitive information, which could lead to financial loss or identity theft.
To combat IVR fraud, it’s crucial to remain vigilant, never share sensitive information over the phone unless certain of the caller’s identity, and hang up on unsolicited calls requesting personal details. Always verify the caller by contacting the organization through official channels.
4. Attempt to Receive Free Replacement Items:
The tactic of attempting to gain free items through call center fraud involves scammers impersonating legitimate customers. They falsely claim that their orders were never received or arrived damaged and then demand refunds or replacements. Typically, these fraudsters request that these replacements or refunds be directed to alternative addresses, bank accounts, or email addresses. This type of fraud not only results in direct financial losses due to the cost of replacements and refunds but also depletes inventory and can negatively impact a company’s bottom line and customer trust.
Why Knowledge-Based Authentication is No Longer Sufficient
Traditional knowledge-based authentication (KBA) methods are becoming increasingly unreliable and more susceptible to exploitation. Some of the reasons why KBA it’s no longer sufficient for call center authentication include high failure rates, easy for fraudsters to compromise, increased call times, and data breach vulnerability.
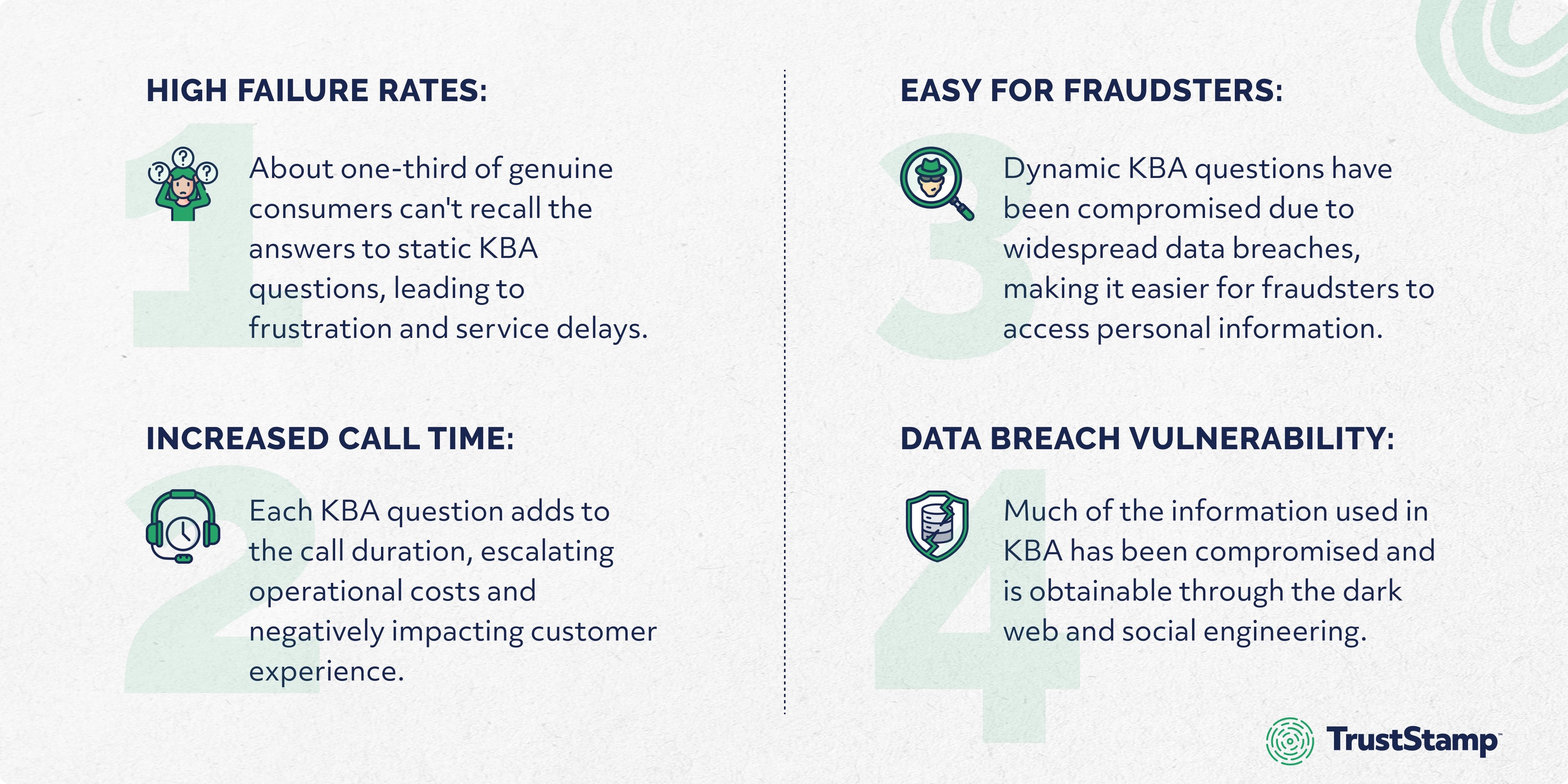
A study suggests that once an account is targeted by fraudsters in a phishing or account takeover attack, the likelihood of a secondary fraud call targeting that account within 60 days is between 33% and 50%. Even after 60 days have passed from the initial attack, the risk of fraud for a previously targeted account remains extremely elevated, between 6% and 9%.
How Trust Stamp Prevents Call Center Fraud
Trust Stamp’s innovative approach to preventing call center fraud addresses the vulnerabilities that fraudsters exploit across various common types of fraud. By integrating advanced biometric technology and secure tokenization processes, Trust Stamp provides a multi-layered defense against unauthorized access and identity theft. Here’s how Trust Stamp specifically addresses each type of fraud mentioned:
1. Account Takeover
Trust Stamp mitigates the risk of Account Takeover fraud through its use of biometric authentication combined with Irreversibly Transformed Identity Tokens (IT2). When a user attempts to access their account, they are required to authenticate themselves with a biometric check, such as a fingerprint or facial recognition, which is then matched against a previously stored biometric token. This process ensures that even if a fraudster has stolen personal identity information (PII), they cannot impersonate the legitimate account holder without the matching biometric data.
2. Card Not Present (CNP) Fraud
For CNP fraud, Trust Stamp leverages its biometric verification system to ensure the person making the transaction is the legitimate cardholder. Before a transaction can proceed, the caller is prompted to provide a biometric sample via a secure method, which is then verified against their stored biometric token. This step adds a critical layer of security that stolen card information alone cannot bypass, effectively neutralizing CNP fraud attempts.
3. IVR Fraud (IVR Mining)
Trust Stamp’s solution to combat IVR Fraud involves integrating biometric verification within the IVR system itself. By incorporating voice biometrics, the system can authenticate the caller’s identity through voice recognition technology. When a caller attempts to access sensitive information or perform account changes via IVR, they must verify their identity through their unique voice pattern. This ensures that only authorized users can access account information, significantly reducing the risk of IVR phishing attacks.
4. Attempt to Receive Free Replacement Items
Trust Stamp addresses the issue of fraudsters attempting to receive free replacement items by requiring biometric authentication for any transaction that involves refunds, replacements, or shipping to new addresses. When a customer requests a replacement or refund, they are prompted to verify their identity through a biometric check. This process ensures that the request is legitimate and not an attempt by a scammer to exploit the system. Additionally, by utilizing IT2 technology, Trust Stamp ensures that any change to customer information or shipping details is authorized by the legitimate account holder, further safeguarding against this type of fraud.
In summary, Trust Stamp’s comprehensive approach, leveraging cutting-edge biometric authentication and IT2 technology, provides a robust defense mechanism against the prevalent types of call center fraud. By ensuring that only authorized users can access and modify account information, Trust Stamp effectively protects against unauthorized access, identity theft, and fraudulent transactions, thus maintaining the integrity of call center operations and customer trust.
How Does it Work?
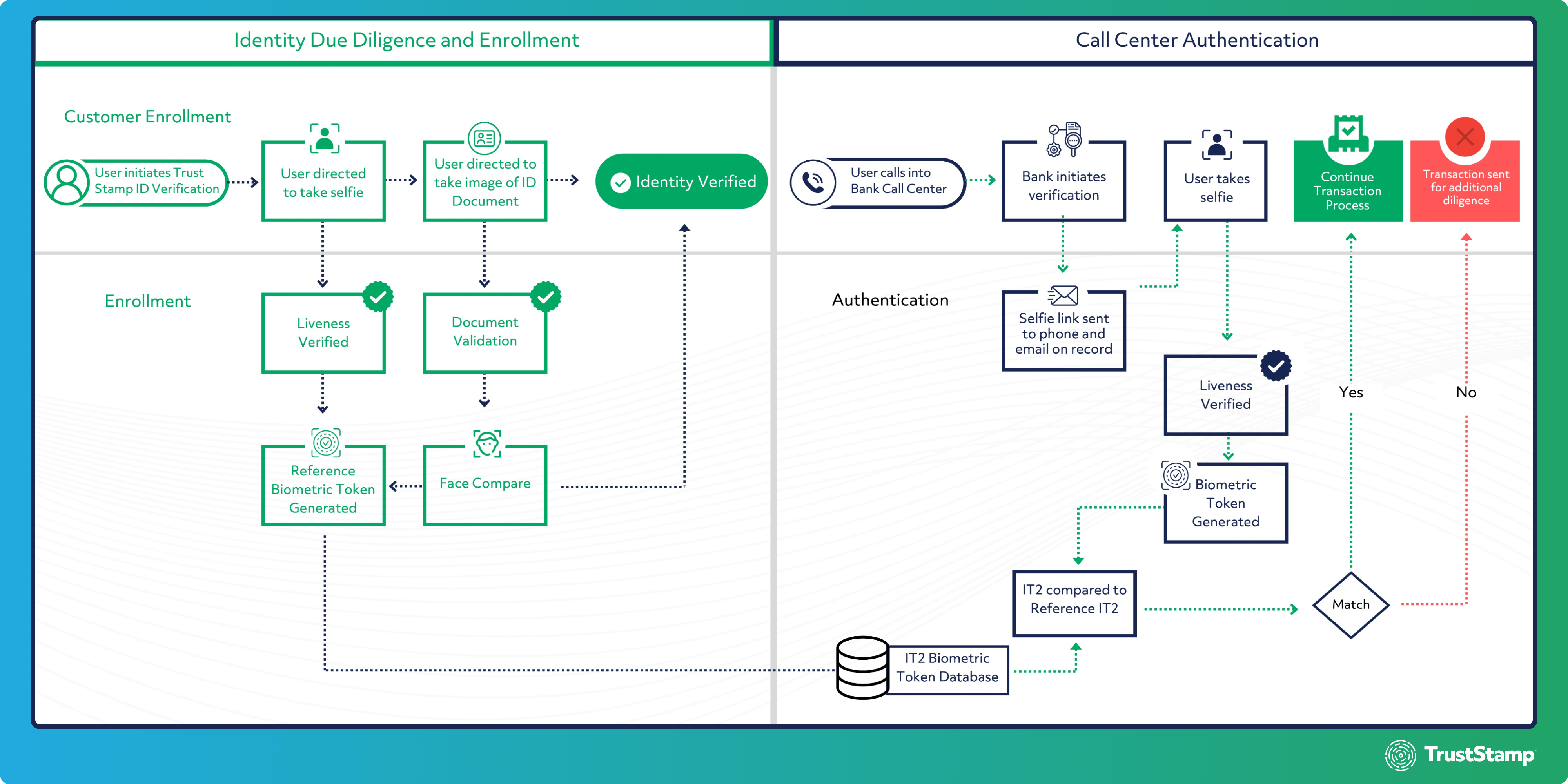
Trust Stamp’s innovative biometric solution transforms how call centers verify customer identities. Our cutting-edge technology ensures efficient and secure customer interactions. Here’s how we can protect your company against call center fraud:
- Possession-Based Authentication: When a customer calls, a unique challenge is sent via email or to a registered phone number, confirming possession of a trusted device.
- Biometric Verification: The customer is prompted to take a live selfie. Trust Stamp’s advanced technology checks for liveness and matches the selfie against a biometric token, ensuring the caller is indeed who they claim to be.
- Seamless Integration: Our solution easily integrates into your existing call center operations, enhancing security without disrupting customer service flow.
Benefits for Financial Institutions
- Cutting-Edge Technology: Utilizing state-of-the-art biometric verification, Trust Stamp ensures the highest security standards are met with ease.
- Reduced Operational Costs: Minimize the time and resources spent on traditional KBA methods, lowering your average handle time (AHT) and operational expenses.
- Improved Customer Satisfaction: Fast and reliable authentication means happier customers and a better overall service experience.
- Adaptable and Flexible: Trust Stamp’s solution is versatile, catering to various call center needs and customer scenarios.
- Data Privacy Assurance with IT2: Trust Stamp’s IT2 technology enables biometric matching while eliminating the risk of privacy and data theft. Unlike traditional biometric systems, IT2 does not require storing biometric data, ensuring enhanced security and compliance with privacy standards.
Join the revolution in call center security and customer service. Contact Trust Stamp today for a demo and see how our biometric solution can transform your authentication process!

