Cyberattacks have become a significant concern for businesses and individuals alike, and the threat continues to grow. With the growing prevalence of cyber threats, the number of claims filed with cyber insurance companies covering these claims is also increasing. In 2022, the US data breach’s average cost reached $9.44 million. Globally, businesses will lose approximately $10.5 trillion in total in 2025 due to cybercrime.
Are you looking for a way to reduce the costs of cyberattacks perpetrated on your policyholders? In this blog, we explore how adding additional security around user authentication, such as a biometric multi-factor authentication (MFA), can substantially mitigate cyber risks.
Common Types of Cyberattacks and How they Work
Some of the most common types cyberattacks perpetrated on companies include phishing and credential stuffing. These attacks can lead to costly and disruptive ransomware attacks. We’ll explore these types of attacks and what can be done to mitigate these risks.
- Phishing Attacks -When a bad actor launches a phishing attack, and the victim gives over sensitive information such as a password or credit card numbers, that’s usually enough to perpetrate an attack. With the user’s login credentials, a fraudster will try to gain access control to company computers and systems. That’s because, a lot of the time, security is limited to just a password. Once access is gained, the attacker can exfiltrate data, perform an account takeover, or perform a ransomware attack.
- Credential Stuffing Attacks – This type of attack falls under brute force attacks. Credential stuffing is a type of cyberattack where attackers use a list of stolen credentials (usernames and passwords) obtained from data breaches to automate login attempts on other websites to gain unauthorized access to user accounts. This is possible because many people reuse the same username and password combination across multiple websites. Like phishing, the attacker uses these credentials to gain access to company computers and systems. Like a phishing attack, once access is gained, the attacker can exfiltrate data, perform an account takeover, or perform a ransomware attack.
- Ransomware Attacks – Once a malicious agent gains access control to a company’s system through a phishing or credential stuffing attack, a common next step is to use malware to encrypt files and demand a ransom payment for the decryption key to restore access to the encrypted files. When the victim company is not prepared, these attacks commonly paralyze the company and leave them unable to continue the business. Note that in the cases of encryption and lockouts, the reopening codes do not always work.
Data encryption has become such a problem that in many cases, victims are now often encouraged not to pay the hacker but rather to report the incident and just take the loss. As a result, hackers using ransomware for data encryption have turned to data theft in addition to or instead of encryption. Before encrypting data, the hacker goes through files in search of sensitive, valuable, and confidential information. They then copy it and use it as leverage to demand ransom payments. When that information can damage a business or its customers, the victim often has no choice but to acquiesce to the demands.
How Does MFA Solve Common Cyberattacks?
Using Multi-Factor Authentication helps defeat phishing and credential-stuffing attacks by requiring multiple identity verification methods to access an account. This typically includes a password and a second authentication factor, such as a one-time code sent to a mobile device or generated by a security token. As an added benefit, now, without a way in, attackers cannot perpetrate the ransomware attack.
Is Traditional MFA Enough?
While traditional multi-factor authentication methods, such as one-time passcodes, is helpful, it isn’t always enough. For example, a malicious agent who already has the victim’s email login information or has gained access to a device may still be able to access that security code. Biometric MFA, because it relies on unique personal characteristics that would be difficult or impossible to replicate or steal, offers better protection against these attacks.
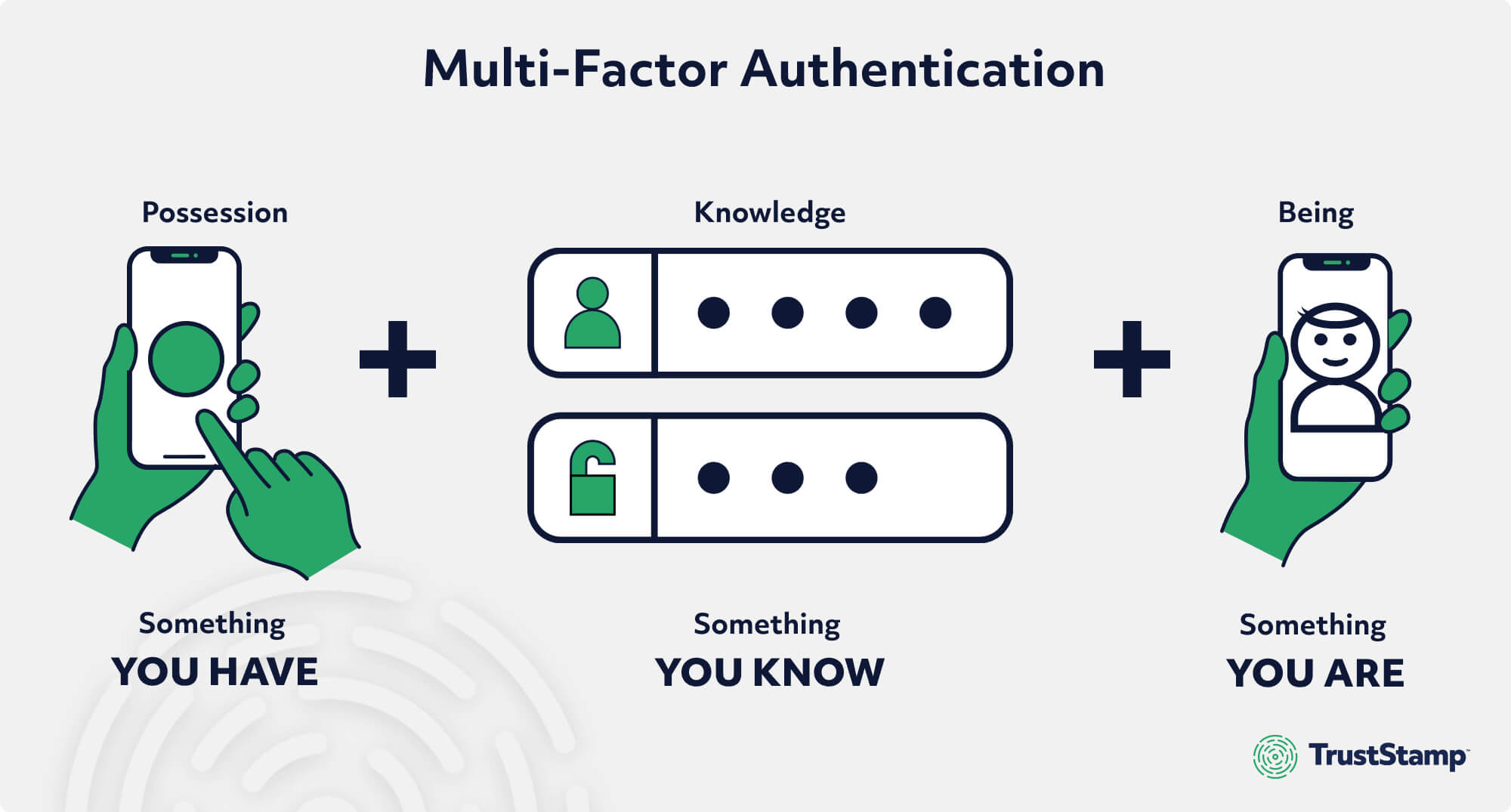
Biometric MFA like that which Trust Stamp offers improves on this even more by adding a third authentication factor. By adding biometric MFA, you now have three authentication factors: 1) Something you know – your password; 2) Something you have – the phone we send a link to and 3) Something you are – your face.
Conclusion
Biometric multi-factor authentication is a necessity in today’s cybersecurity landscape. Compared to traditional MFA methods, it not only helps organizations prevent fraud and identity theft, but it’s also more convenient for users and more compliant with regulatory standards.
Cyber insurance companies should take a proactive approach in promoting its use to protect their policyholders and themselves from cyberattacks.
Upgrade your security today with Biometric MFA! Contact Trust Stamp now to learn more.

