Digital Communities Have Unique Identity Needs
Today, the very notion of ‘community’ has undergone a radical transformation. Communities driven by shared interests, passions, and identities breathe life into diverse online platforms. These spaces provide a haven for these communities to connect and thrive. While these communities offer unprecedented opportunities for connection and collaboration, they also present unique challenges in terms of identity and security.
81% of communities saw their visibility increase over the last two years, 67% of them with an added increase in urgency: the COVID-19 pandemic moved online communities from a nice-to-have to a must-have.
The Double-Edged Sword of Anonymity
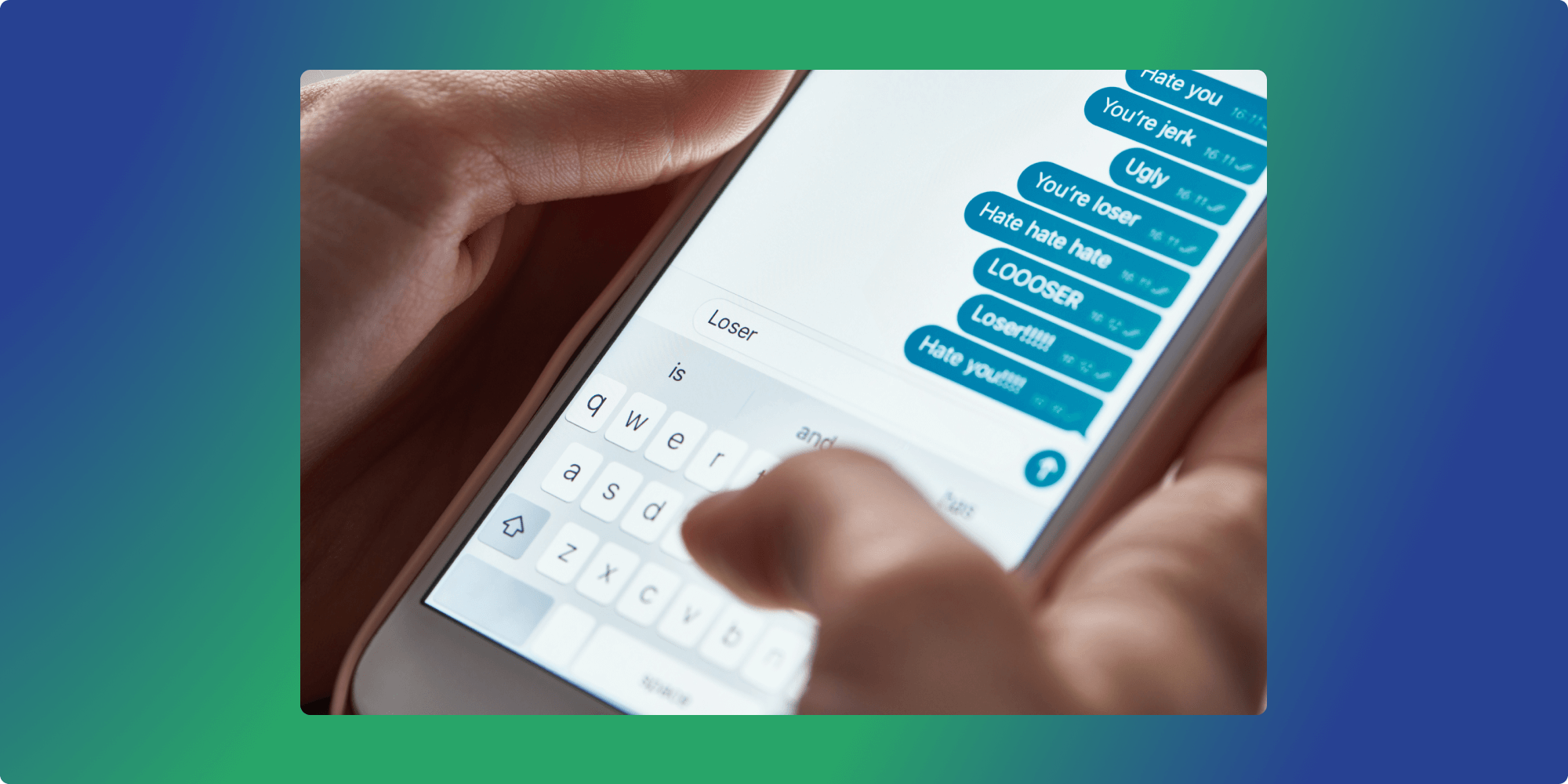
While the digital space offers a haven of privacy for many groups, including LGBTQIA+, SA targets and survivors, oppressed cultures, and political dissidents, this very shield of anonymity can also be weaponized. The protective cloak of privacy increases user safety. Paradoxically, this same cloak protects threat actors while they work to undermine community trust.
Their arsenal:
- The Clandestine Club – Cyberbullying and Cyber Abuse: Anonymity and global reach allow people and groups to bully and abuse others with little to no repercussions. This age-old menace is now magnified in the digital sphere.
- The Glamour – Image-based Abuse: The unauthorized sharing or manipulation of personal images and likenesses. Whether this is used to create non-consensual intimate imagery (NCII), for romance-based scams, or to steal credibility for disinformation dissemination, teams need a way to see when the same likeness is associated with multiple accounts.
- The Megaphone- Disinformation Amplification: Using anonymity to spread falsehoods. Individuals and groups create “voting blocs” to modify algorithmic exposure and make their views appear more socially supported.
The Implicit Trust in Digital Platforms & the Threat of Stolen Likenesses

When individuals sign up for a digital platform, they’re not merely creating an account. They’re placing their trust in that platform’s Trust & Safety teams, believing in a promise of security. While platforms may strive to uphold this trust, their protective measures are often as varied as their corporate values and digital ethos.
One of the more insidious means threat actors employ to undermine digital security is pilfering someone else’s likeness. By assuming another’s digital identity, they can perpetrate various malicious activities, from romance scams to reputation hijacking, all while evading detection.
Limitations of Standard Detection Tools
Relying on age-old, legacy products poses a significant challenge in this game of digital cat and mouse. These tools often falter when confronted with modern image manipulations. Whether it’s subtle changes brought about by filters, variations in lighting, cosmetic alterations, or image obstructions, legacy tools frequently miss the mark.
In our analysis, the types of manipulations threat actors use to reduce detection are:
- Filter
- Change in Hair & Makeup
- Black & White Filter
- Change in Hair & Makeup
- Poorly Lit Photo
- Mirror Selfie
- Face Partially Obscured
- Not-Head-On Shot
- Face Obscured by Mask
- Selfie with Text Overlay
- Clipped Highlights
- Face Partially Cropped
- Face Not Primary in Photo
Trust Stamp Unsupervised Biometrics: A Game Changer
To address this, Trust Stamp’s Dr. Norman Poh and his team have developed new AI tooling that can quickly process large image sets and identify when the same biometrics show up. Recent tests show a 3.6X improvement in duplicate detection vs legacy tooling.
Trust Stamp’s proprietary system represents a paradigm shift in the world of identity verification, distinguished by its adaptive evolution. Not only does the system benefit from each interaction, refining its mechanisms with every use, but it also possesses the unique capability to self-correct, addressing any prior inaccuracies. This results in an ever-improving mechanism, perpetually enhancing its accuracy and reliability with each new interaction.
This technology can be applied to defeat threats such as ‘Catfishing’, where the likeness of an individual is stolen and often repeated over and over. Trust Stamp’s system quickly identifies these duplicates and stops the threat.
Ensuring Equity
In the realm of biometrics, equity is non-negotiable. Trust Stamp actively addresses potential biases in facial recognition technology, championing the imperative that such systems must maintain unwavering accuracy across diverse skin tones. A testament to this commitment is Trust Stamp’s R&D office in Rwanda, Africa. This center of innovation, staffed with engineers from multiple African nations, underlines the company’s dedication to fostering diversity in its team and its technology.
The Trust Stamp Initiative
Trust Stamp recognizes the chasm between current detection capabilities and the needs of modern digital platforms. As an invitation to platforms committed to enhancing user security, Trust Stamp offers to conduct a comprehensive assessment on 6,000-10,000 images at zero cost. This will provide a tangible measure of the current tooling’s efficacy against likeness theft.
Secure your spot now and elevate your fraud prevention strategy.

